Working from home is now forever for a lot of companies, which comes with perks such as more flexibility, lower costs, and a broader talent pool from which to choose.
But with that model change, however, come intrusiveness and security risks that CISOs now must manage. Given the growing remote work population, creating a culture of secure remote work is key for protecting data and enabling businesses to carry on.
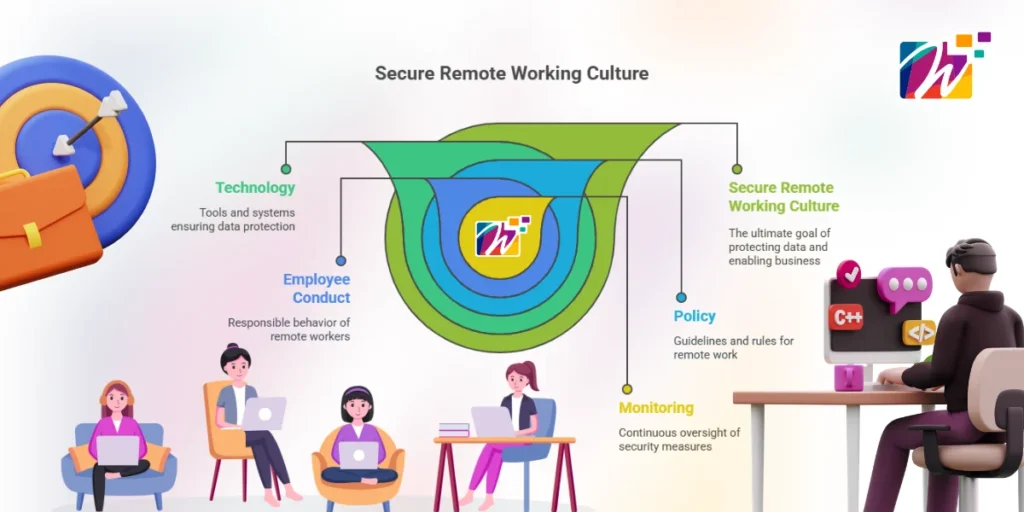
For the Chief Information Security Officers (CISOs), forming a secure remote working culture is not just a technical requirement, but a business concern as well. It is not sufficient to integrate solutions all at once. It involves a cohesive system of technology, policy, employee conduct, and unrelenting monitoring.
In this blog, we will uncover the fundamentals of a secure remote working culture and share a checklist for CISOs to consider.
Understanding the Risks of Remote Work
The geopolitical changes of work from home policies have altered the structure of most companies entirely. Although the remote model has its advantages, such as a higher level of structural flexibility, better scalability, higher quality workforce internationally, and increased talent availability, it also poses serious cybersecurity concerns.
A CISCO’s major concern is that unlike any other form of working, constructing a safe remotely functioning office culture transcends just a technical concern—it’s a pivotal strategy that must be observed.
In advance of the checklist lies the necessity to realize the dangers posed by working remotely. A few but quite critical dangers are:

- Unsecured networks: Many remote workers access the internet via public WiFi or an unsecured home network, which allows an increased chance that hackers can intercept the information that is being transmitted.
- Device risk: Business use of personal devices might not be as secure as if company devices were used, leaving them vulnerable to malware and other attacks.
- Phishing: In the context of working remotely, the company can neglect phishing attacks somewhat, which can lead to confidentiality violations.
- Data breaches: There is a higher risk of data breaches with the work-from-home setup, especially if confidential information is either kept in individual devices or sent via non-secured networks.
To lessen these threats and create a secure working-from-distance environment, CISOs should follow this comprehensive checklist:
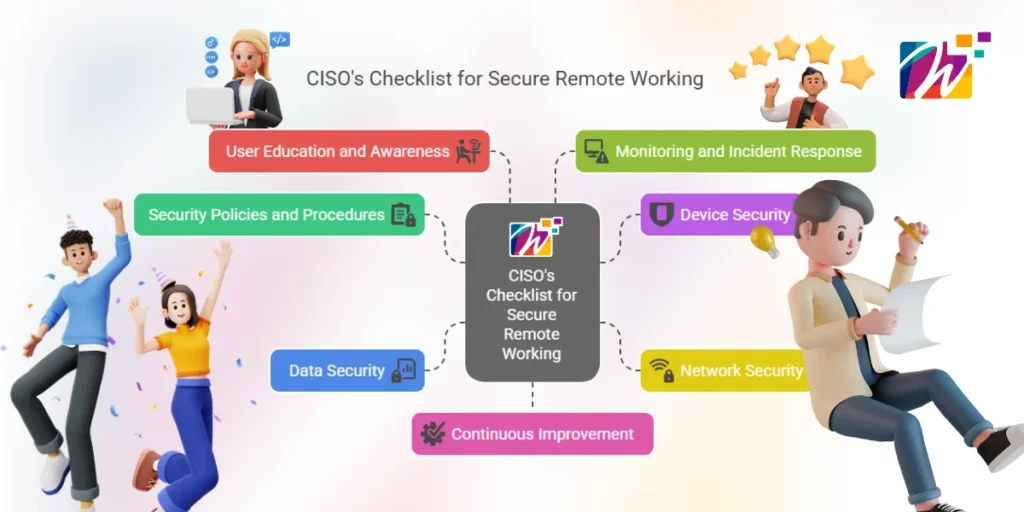
1. Security Policies and Procedures
- Establish a remote work policy: Establish specific remote work policies, including security requirements and the conditions under which remote work is acceptable.
- Refine current policies: Assess and refine current security policies to include remote work.
- Define incident response procedures: Develop procedures for responding to security incidents that may occur while working remotely.
2. Device Security
- Use device management: Employ shared and company-owned device management solutions to protect your company’s devices.
- Mandate that devices are encrypted: Make sure all work devices are encrypted so information is protected.
- Audit your devices: Regularly check and see if your device complies.
3. Network Security
- Use VPNs: Make employees at home use virtual private networks (VPNs) to encrypt internet connections.
- Secure Wi-Fi: Make sure your remote staff is using secure Wi-Fi or give them instructions on how to secure their home networks.
- Track the network: Track network activity to detect anything odd.
4. Data Security
- Encrypt the data: All sensitive data must be encrypted at rest and in transit.
- Secure your data storage: Prevent sensitive data leakage with the cloud or other data storage capabilities.
- Restrict data access: Restrict those people who have access to sensitive data to those who need it.
5. User Education and Awareness
- Offer security training: Regular security training for staff working from home, on things like how to spot phishing emails and ways to secure devices and networks.
- Perform phishing simulations: Run phishing simulations to assess the knowledge and responses of your remote workers.
- Promote reporting: Encourage your remote staff to report anomalies or security incidents.
6. Monitoring and Incident Response
- Remote access behavior: Keep an eye on what users are doing remotely.
- Create incident response processes: Create processes to follow if you suffer a security incident when working remotely.
- Test incident response: Practice responding to security incidents to verify your effectiveness
7. Continuous Improvement
- Revision of security policies: Ensure that the security policies are reviewed at regular intervals so that they are up-to-date and serve their purpose in protecting the information.
- Conduct security audits: It is recommended to schedule security audits for your system in order to detect weaknesses and gaps.
- Keep in the know about new threats: Keep up-to-date with new threats, and change security measures to keep up with them.
Conclusion:
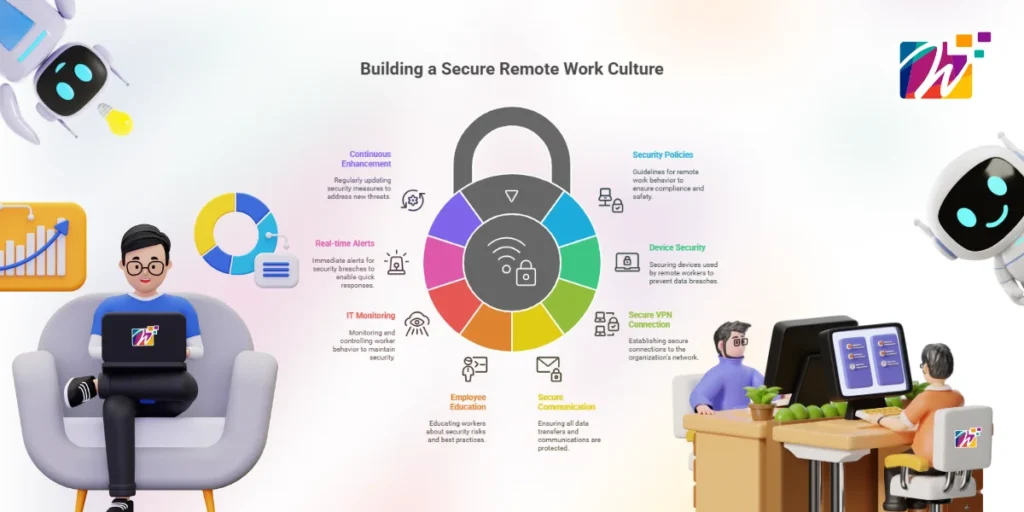
To establish a secure remote work culture, various measures must be implemented. These policies inform the workers about the behaviors they should adopt when working remotely.
This entails securing all the devices that workers use at home or elsewhere to facilitate their work. A secure Virtual Private Network (VPN) connection is needed to establish a secure connection with the organization’s network. All communication, data transfers, and any other file-sharing action must be secure.
Employers should educate their workers and make them aware of the risks that they are exposed to each time they handle their data and the data of their employer. IT administrators should monitor and control the behavior of their workers during remote work.
All employees and employers need to know the immediate, real-time consequences anytime a user breaks a security rule and causes an alert to counter it — instantly. Against that list, CISOs can defend sensitive data and help keep businesses running in a work-from-home world. Or remember that security is a process and you need to continue enhancing it as new possible ways of attacking your services become available.
Recommendations for CISOs
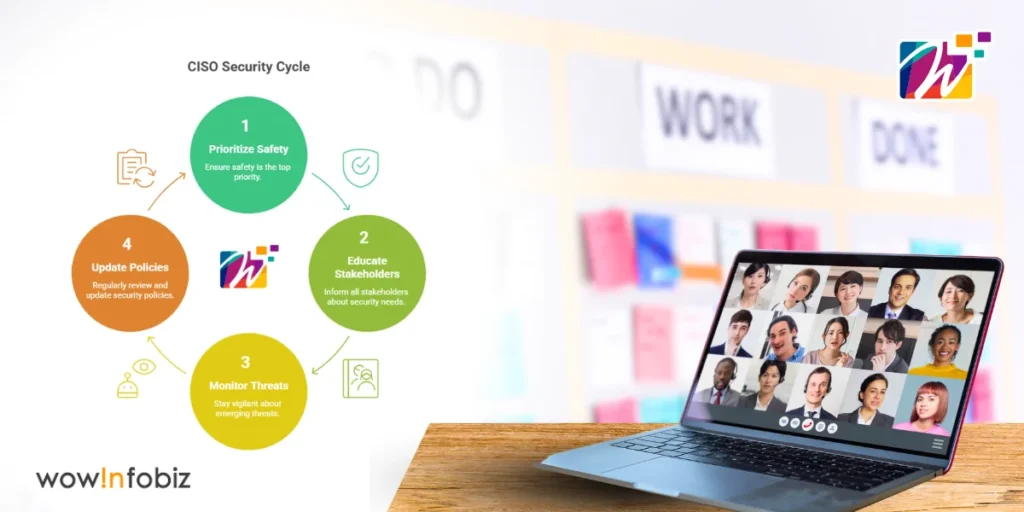
- Safety first: Prioritize safety in your company.
- Speak to all stakeholders: Educate remote workers, stakeholders, and leadership about what security is needed and expected.
- Be aware: Be aware of threats and adapt security measures accordingly.
- Always review and update security policies: A policy that was written a year ago may no longer provide the same level of security and can even open up a backdoor.
By adhering to these practices and the checklist provided above, CISOs can foster a safe remote working culture that safeguards sensitive information as well as business continuity.




